Threat Actors
The entity responsible for an event that has an impact on the safety of another entity
- Also called a malicious actor
Threat actor attributes
- Describes characteristics of the attacker
Useful to categorize the motivation
- Why is this attack happening?
- Is this directed or random?
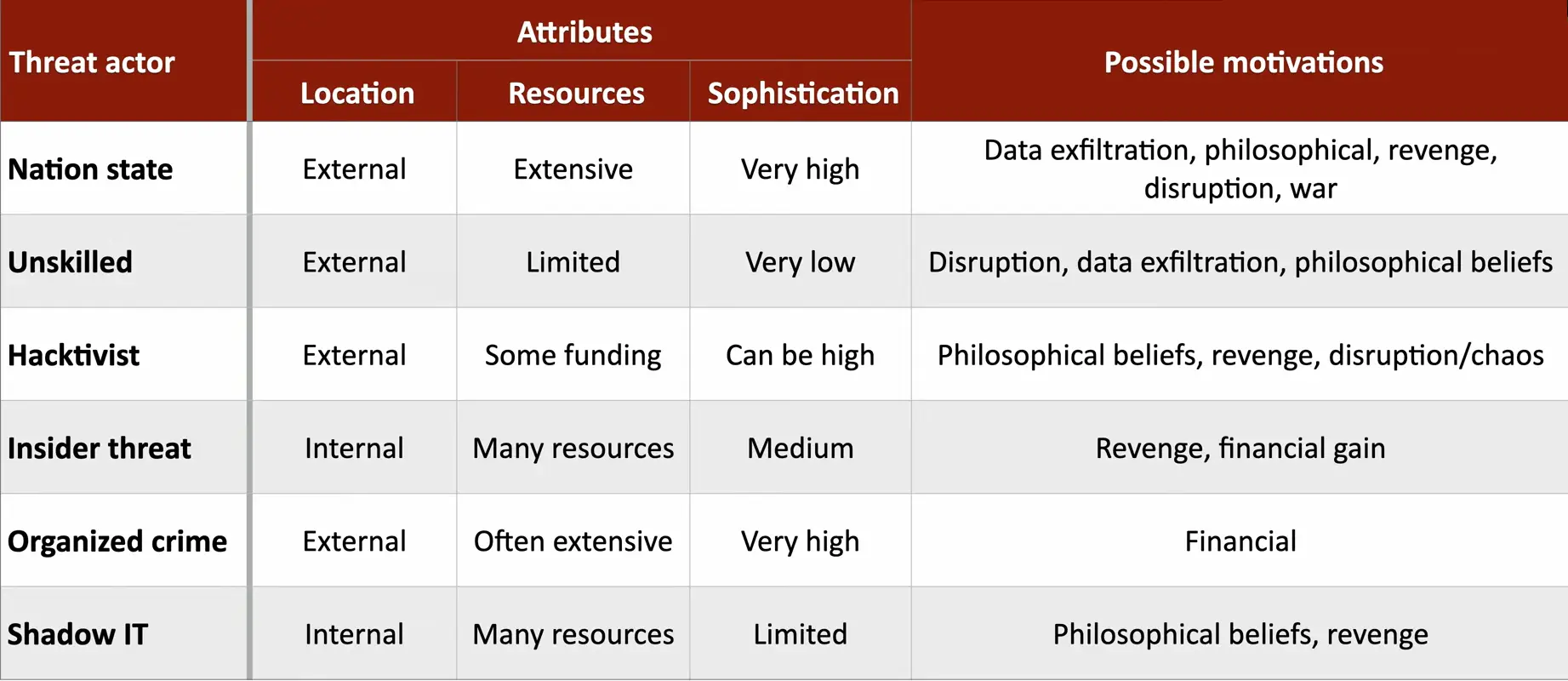
Attributes of Threat Actors
Internal/external
- The attacker is insider the house
- They are outside and trying to get in
Resources/funding
- No money
- Extensive funding
Level of sophistication/capability
- Blindly runs scripts or automated vulnerability scans
- Can write their own attack malware and scripts
Motivations of Threat Actors
What makes them tick?
- There is a purpose to this attack
Motivation include
- Data exfiltration
- Espionage
- Service disruption
- Blackmail
- Financial gain
- Philosophical/political beliefs
- Ethical
- Revenge
- Disruption/chaos
- War
Nation States
External entity
- Government and national security
Many possible motivations
- Data exfiltration, philosophical, revenge, disruption, war
Constant attacks, massive resources
- Commonly an Advanced Persistent Threat (APT)
Highest sophistication
- Military control, utilities, financial control
- United States and Israel destroyed 1000 nuclear centrifuges with the Stuxnet worm
Unskilled Attackers
Run pre-made scripts without any knowledge of what’s really happening
- Anyone can do this
Motivated by the hunt
- Disruption, data exfiltration, sometimes philosophical
Can be internal or external
- But usually external
Not very sophisticated
- Limited resources, if any
No formal funding
- Looking for low-hanging fruit
Hacktivist
A hacker with a purpose
- Motivated by philosophy, revenge, disruption, etc.
Often an external entity
- Could potentially infiltrate to also be an insider threat
Can be remarkably sophisticated
- Very specific hacks
- DoS, website defacing, private documents release
Funding may be limited
- Some organizations have fundraising options
Insider Threat
More than just passwords on sticky notes
- Motivated by revenge, financial gain
Extensive resources
- Using the organization’s resources against themselves
An internal entity
- Eating away from the inside
Medium level of sophistication
- The insider has institutional knowledge
- Attacks can be directed at vulnerable systems
- The insider knows what to hit
Organized Crime
Professional criminals
- Motivated by money
- Almost always an external entity
Very sophisticated
- Best hacking money can buy
Crime that’s organized
- One person hacks, one person manages the exploits, another person sells the data, another handles’ customer support
Lots of capital to fund hacking efforts
Shadow IT
Going rogue
- Working around the internal IT organization
- Builds their own infrastructure
Information Technology can put up roadblocks
- Shadow IT is unencumbered
- Use the cloud
- Might also be able to innovate
Limited resources
- Company budget
Medium sophistication
- May not have IT training or knowledge