Security Controls
- Security risks are out there
- Many categories and types to consider
- Assets are also varied
- Data, physically property, computer systems
- Prevent security events, minimize the impact, and limit the damage
- Security controls
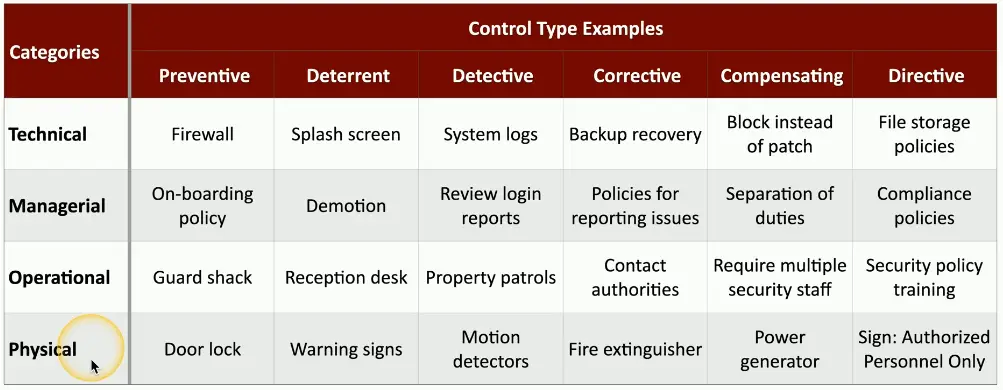
Control Categories
- Technical Controls
- Controls implemented using systems
- OSes controls
- Firewalls, anti-viruses
- Managerial Controls
- Admin controls associated with security design and implementation
- Security policies, SOPs
- Operational Controls
- Controls implemented by people instead of systems
- Security guards, awareness programs
- Physical Controls
- Limit physical access
- Guard shack
- Fences, locks
- Badge readers
Preventive Control Types
- Preventive
- Block access to a resource
- You shall not pass
- Prevent access
- Firewall rules
- Follow security policy
- Guard shack checks all identification
- Enable door locks
Deterrent Control Types
- Deterrent
- Discourage an intrusion attempt
- Doesn’t directly prevent access
- Make an attacker think twice
- Application splash screens
- Threat of demotion
- Front reception desk
- Posted warning signs
Detective Control Types
- Detective
- Identify and log an intrusion attempt
- May not prevent access
- Find the issue
- Collect and review system logs
- Review login reports
- Regularly patrol the property
- Enable motion detectors
Corrective Control Types
- Corrective
- Apply a control after an event has been detected
- Reverse the impact of an event
- Continue operating with minimal downtime
- Correct the problem
- Restoring from backups can mitigate a ransomware infection
- Create policies for reporting security issues
- Contact law enforcement to manage criminal activity
- Use a fire extinguisher
Compensating Control Types
- Compensating
- Control using other means
- Existing controls aren’t sufficient
- May be temporary
- Prevent the exploitation of a weakness
- Firewall blocks a specific application instead of patching the app
- Implement a separation of duties
- Require simultaneous guard duties
- Generator used after power outage
Directive Control Types
-
Direct a subject towards security compliance
-
A relatively weak security control
-
Do this, please!!!
- Store all sensitive files in a protected folder
- Create compliance policies and procedures
- Train users on proper security policy
- Post a sign for “Authorized Personnel Only”
Managing Security Controls
- These are not inclusive lists
- There are many categories of control
- Some organizations will combine types
- There are multiple security controls for each category and type
- Some security controls may exist in multiple types or categories
- New security controls are created as systems and processes evolve
- Your organization may use very different controls